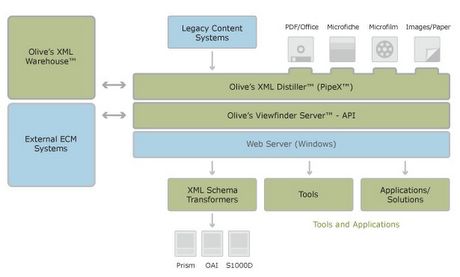
Lawyers for AT&T accidentally released sensitive information while defending a lawsuit that accuses the company of facilitating a government wiretapping program, CNET News.com has learned.
AT&T's attorneys this week filed a 25-page legal brief striped with thick black lines that were intended to obscure portions of three pages and render them unreadable (click here for PDF).
But the obscured text nevertheless can be copied and pasted inside some PDF readers, including Preview under Apple Computer's OS X and the xpdf utility used with X11. More here.
Oh, and...
Think AT&T's complicity in helping the NSA spy on America
doesn't affect you? Think again.
Here are the cities that have facilities in
which AT&T/NSA can install (or already has installed) gear to spy on
Americans:
AT&T Central Office Locations
Arlington, VA (ARTNVACK)
Atlanta, GA (ATLNGATL)
Cambridge, MA (CMBRMA01)
Chicago, IL (CHCGILCL)
Cleveland, OH (CLEVOH02)
Columbus, OH (CLMBOH11)
Dallas, TX (DLLSTXTL)
Dayton, OH (DYTNOH15)
Denver, CO (DNVRCOMA)
Detroit, MI (DTRTMIBA)
Honolulu, HI (HNLLHIWP)
Houston, TX (HSTNTX01)
Indianapolis, IN (IPLSINAT)
Kansas City, MO (KSCYMO09)
Los Angeles, CA (LSANCA02)
Confirmed by KleinMemphis, TN (MMPHTNMA)
Miami, FL (MIAMFLAC)
Milwaukee, WI (MILWWIHE)
Minneapolis, MN (MPLSMNDT)
New Orleans, LA (NWORLAMA)
New York City, NY (NYCMNY54)
New York City, NY (NYCMNYBW)
Newark, NJ (NWRKNJ02)
Oakbrook, IL (OKBRILOA)
Oakland, CA (OKLDCA03)
Ojus, FL (OJUSFLTL)
Philadelphia, PA (PHLAPASL)
Phoenix, AZ (PHNXAZMA)
Pittsburgh, PA (PITBPADG)
Portland, OR (PTLDOR62)
Redwood City, CA (RDCYCA02)
Rochester, NY (ROCHNYXA)
Sacramento, CA (SCRMCA01)
San Antonio, TX (SNANTXCA)
Salt Lake City, UT (SLKCUTMA)
San Diego, CA (SNDGCA02)
Confirmed by KleinSan Francisco, CA (SNFCCA01)
Confirmed by KleinSan Francisco, CA (SNFCCA21)
Confirmed by KleinSan Jose, CA (SNJSCA02)
Confirmed by KleinSan Juan, PR (SNJNPRZA)
Seattle, WA (STTLWA06)
Confirmed by Klein*St. Louis, MO (STLSMO09)
Sherman Oaks, CA (SHOKCA02)
Tulsa, OK (TULSOKTB)
Tucson, AZ (TCSNAZMA)
Washington, DC (WASHDCSW)
West Palm Beach, FL (WPBHFLAN)
White Plains, NY (WHPLNY02)
No worries right? You only make local calls. AT&T provides local service in
at least these locations:
Cleveland, OH (CLEVOH02)
Detroit, MI (DTRTMIBA)
Indianapolis, IN (IPLSINAT)
Los Angeles, CA (LSANCA02)
San Antonio, TX (SNANTXCA)
St. Louis, MO (STLSMO09)
And they provide circuits for nearly all of the newer local providers.
Not concerned yet because you only use EMAIL at work, or browse the internet at work? Does your employer buy private data circuits from AT&T to connect them to the internet? Most likely. As does every company and government in the world.
http://www.att.com/gov/solution/network_services/data_nw/def.html
Or perhaps because you didn't find yourself on the list of cities above you are fine. Your phone/internet/corporate traffic isn't compromised because you:
a) Only use AT&T for long distanceb) Use another long distance/internet company(that, unbeknownst to you buys circuits from AT&T for your area)c) Have never done anything requiring privacy in your lifed) Thought your cell phone simply had the range to talk all over the country directly (sorry, couldn't help it)
Here is AT&T's world. And it is impressive.
http://www.att.com/globalnetworking/media/network_map.swf
Drill down. They have all these dots because they were a government regulated monopoly for nearly 75 years. If you were born after 1980 you might not know that. They were the most respected telecommunications company in the world.
That's how you develop a service offering like this.
http://www.att.com/globalnetworking/media/network_map.swf
AT&T is the data on-ramp for the world. Your phone calls are just data. And all the content is recordable, not just call detail information, when using the equipment deployed by the NSA in AT&T's central offices.
Did you happen to notice Cleveland on that list? Here's a tin foil thought to leave you with. While we've been so focused on Diebold, we've neglected to discuss how those electronic results are transmitted to central sites for tabulation. I'm not suggesting this took place, but if you have a product that can do this (currently installed and in use by the NSA at these some of these AT&T locations):
Unparalleled extensibility — NarusInsight’s functionality can easily be configured to feed a particular activity or IP service such as security, lawful intercept or even Skype detection and blocking.
More on Narsus here.
Then you have a product that can block, i.e prevent, data packets from reaching their destination. If you can prevent them from reaching their destination, you can alter the packet content, and then send them on their way to the original destination.
Of course Klein in his AT&T disclosure indicated that the fiber optics were cut in a way that doesn't put this equipment in the primary data flow. Who really knows what happens in a central office in the dead of night during an election year.
Silly me, I forgot. Republican Senator Robertson is providing oversight. Whew! I feel much better now.
Still think none of this affects you?